Infection Chain:

Figure 1: Infection chain of the phishing campaign
On October 16th, the email below was sent with subjects such as “Invoice for” (random digits followed by it) and matching attachments like “Invoice_23794.16_10.doc”. The attachments were office documents with VB macros in it. We observed two sets of emails tricking users to believe it’s from legitimate source. One claims that it has been scanned by the Symantec Email Security and the other claims that it’s coming from DocuSign signature service.
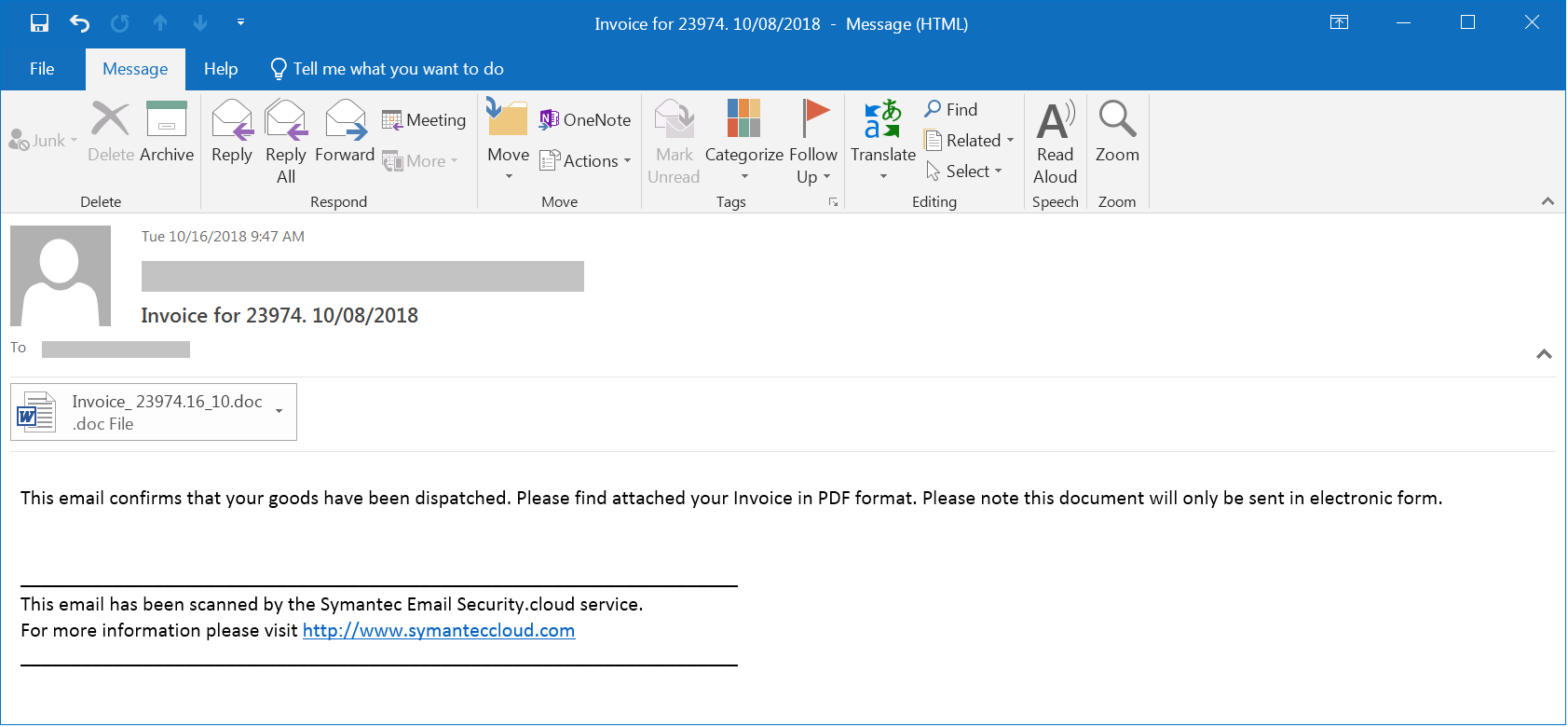
Figure 2: Email used in phishing campaign
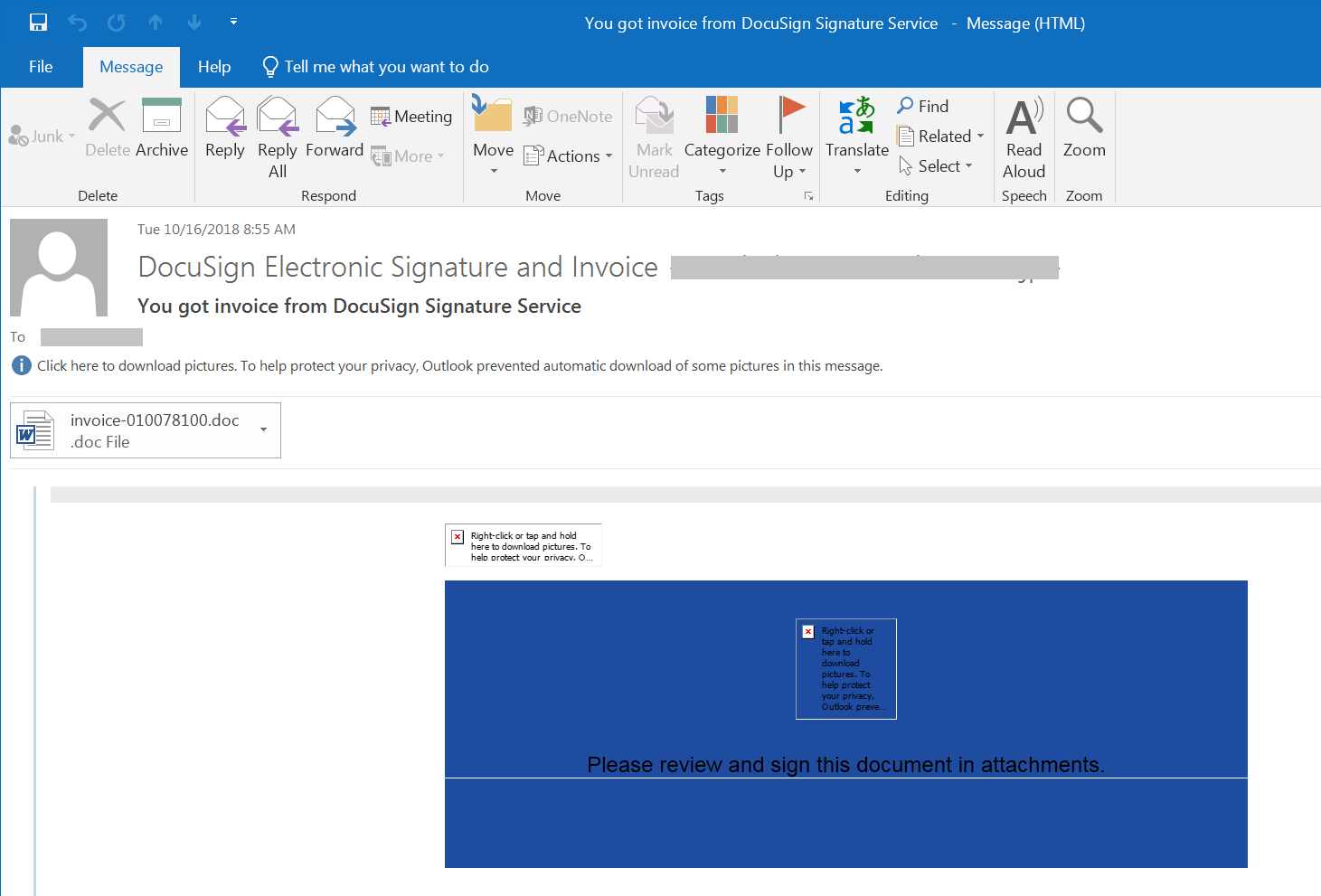
Figure 3: Email used in phishing campaign
Upon launching the attachment, it tells the user that the document was created in earlier version of Microsoft office and requests to click ‘Enable content’ to view the content properly. Even more, the page below has been crafted to look like it has some display issues.

Figure 4: Invoice document
If the recipient falls for the lure and enables content, the malicious macro code shown below runs and launches a command to download the initial payload. The payload, an installer file, is then run

Comments
0 comments
Please sign in to leave a comment.